-


Security
/ 2 weeks agoEarly Decisions in First 90 Seconds Critical to Incident Response
The initial moments following the detection of a security breach are now widely regarded as the most critical phase of any...
-

Security
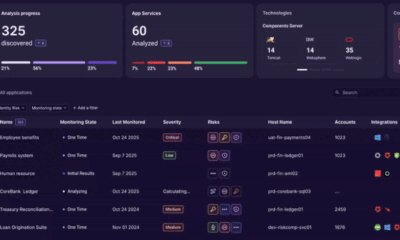
/ 2 weeks agoOrchid Security Launches Continuous Identity Observability Platform
A cybersecurity firm has introduced a new platform designed to provide continuous monitoring of identity usage within enterprise software applications. The...
-
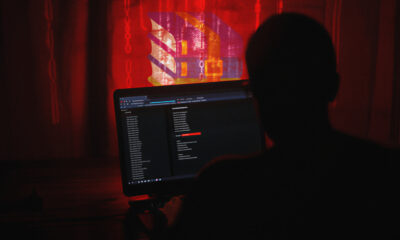

Security
/ 2 weeks agoChina-Linked Hackers Exploit WinRAR Flaw in Southeast Asia Espionage
Security researchers have identified a new cyber espionage campaign targeting government and law enforcement agencies across Southeast Asia throughout 2025. The...
-


Security
/ 2 weeks agoDEAD#VAX Malware Uses IPFS VHD Files to Deploy AsyncRAT
Security researchers have uncovered a sophisticated malware campaign, identified as DEAD#VAX, which uses a novel combination of legitimate system features and...
-

Security
/ 2 weeks agoMicrosoft Develops AI Scanner to Detect Model Backdoors
On Wednesday, Microsoft announced the development of a new security tool designed to identify hidden backdoors in publicly available large language...
-


Security
/ 2 weeks agoSolarWinds Web Help Desk Flaw Added to CISA’s Exploited List
The U.S. cybersecurity and Infrastructure Security Agency (CISA) has added a critical vulnerability in SolarWinds Web Help Desk software to its...
-


Security
/ 2 weeks agoEclipse Foundation to Enforce Security Checks for VS Code Extensions
The Eclipse Foundation has announced a mandatory security review process for all extensions before they are published to the Open VSX...
-


Security
/ 2 weeks agoMicrosoft Warns of Python Infostealers Targeting macOS
Microsoft has issued a warning that information-stealing malware campaigns are increasingly targeting Apple’s macOS operating system. The tech giant’s security researchers...
-


Security
/ 2 weeks agoAPT28 Exploits Microsoft Office Flaw in European Cyberattacks
A Russia-linked state-sponsored hacking group has been observed exploiting a newly disclosed vulnerability in Microsoft Office software in targeted attacks across...
-


Security
/ 2 weeks agoMajor Cloud Outages Disrupt Global Internet Services
Major cloud computing providers have experienced a series of significant service disruptions in recent months, causing widespread outages across the internet....



















