-
Security
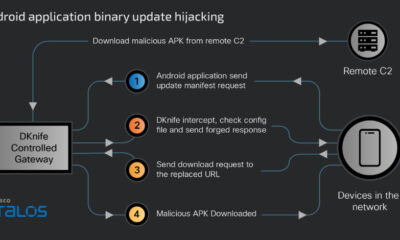
/ 2 weeks agoChina-Linked DKnife Framework Hijacks Router Traffic for Malware
cybersecurity researchers have exposed a sophisticated adversary-in-the-middle framework, known as DKnife, which has been operated by threat actors linked to China...
-


Security
/ 2 weeks agoAI Model Discovers 500+ Critical Flaws in Open-Source Libraries
An artificial intelligence system has identified more than 500 previously unknown, high-severity security vulnerabilities across widely used open-source software libraries. The...
-


Security
/ 2 weeks agoCompromised dYdX npm and PyPI Packages Deliver Malware
Cybersecurity researchers have identified a software supply chain attack targeting developers working with the dYdX decentralized exchange. Malicious actors have compromised...
-


Security
/ 2 weeks agoSamsung Knox Addresses Mobile Security in Evolving Enterprise Networks
Enterprise network security has undergone significant evolution over the past decade, with more intelligent firewalls, advanced threat detection, and detailed access...
-


Security
/ 2 weeks agoIranian Hackers Resume Operations with New Infrastructure
A sophisticated Iranian cyber threat group has resumed its activities with updated infrastructure, following a period of reduced visibility that coincided...
-

Security
/ 2 weeks agoAI Security Gap Widens as Enterprise Use Outpaces Controls
A significant gap has emerged between the rapid adoption of artificial intelligence tools in business environments and the security measures designed...
-


Security
/ 2 weeks agoCybersecurity Threats Emerge from Developer Tools and Cloud Services
Security researchers have identified a series of emerging cyber threats targeting software development environments, remote administration tools, and cloud infrastructure. These...
-

Security
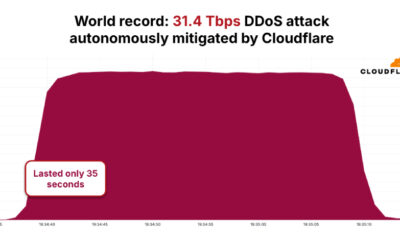
/ 2 weeks agoBotnet Sets Record with 31.4 Tbps DDoS Attack
A distributed denial-of-service botnet known as AISURU or Kimwolf has been linked to a record-breaking cyberattack that reached a peak of...
-


Security
/ 2 weeks agoMalicious NGINX Configurations Hijack Web Traffic
cybersecurity researchers have uncovered an ongoing, large-scale campaign that is hijacking web traffic by compromising NGINX web servers and related management...
-
Security
/ 2 weeks agoCritical n8n Vulnerability Allows Remote Code Execution
A critical security vulnerability in the popular n8n workflow automation platform could allow attackers to execute arbitrary system commands on affected...



















