-


Security
/ 2 days agoHands-On NDR Training Provides Insight into Network Security Operations
A recent Hands-On training session with a Network Detection and Response (NDR) platform offered a practical look into the tools and...
-

Security
/ 2 days agoTrojanized Oura MCP Server Deploys StealC Infostealer
cybersecurity researchers have identified a new campaign distributing the SmartLoader malware, which uses a trojanized version of a legitimate Model Context...
-

Security
/ 2 days agoAndroid Tablet Firmware Backdoor Found in Signed Updates
Security researchers have discovered a sophisticated backdoor embedded within the firmware of several Android tablet brands. The malware, which is distributed...
-


Security
/ 2 days agoAI Assistants Exploited as Malware Command Hubs
cybersecurity researchers have revealed that popular artificial intelligence assistants can be manipulated to act as covert communication channels for malware. This...
-


Security
/ 2 days agoModern SOC Teams Use AI for Faster Cloud Breach Investigations
Security operations center teams are increasingly adopting artificial intelligence and contextual data analysis to accelerate investigations into cloud based breaches, according...
-
Security
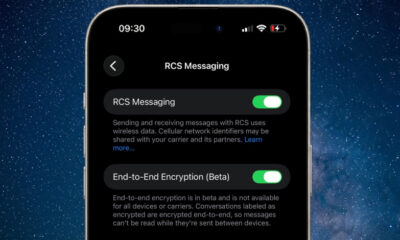
/ 2 days agoApple Tests Encrypted RCS Messaging in iOS Beta
Apple has introduced a significant upgrade to its messaging infrastructure by enabling end-to-end encryption for RCS communications in its latest developer...
-


Security
/ 3 days agoNew ZeroDayRAT Mobile Spyware Threatens Android and iOS Users
cybersecurity researchers have uncovered a new and sophisticated mobile spyware platform being actively marketed to potential buyers. The malware, known as...
-


Security
/ 3 days agoLithuania Launches Mission to Combat AI Cyber Fraud
A consortium led by Kaunas University of Technology (KTU) presented its mission to build a safe and inclusive digital society at...
-


Security
/ 3 days agoWeekly Security Recap: Add-In Hijacks, Zero-Days, Botnets
Security researchers have documented a significant shift in cyberattack strategies over the past week, where trusted software tools and established workflows...
-


Security
/ 3 days agoMajor Password Managers Vulnerable to Recovery Attacks
A recent academic study has identified significant vulnerabilities in several leading cloud-based password management services. The research found that under specific...



















