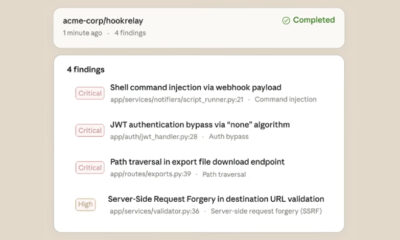
Google-owned cybersecurity firm Mandiant reported on Friday that it has identified a significant expansion in threat activity using tactics consistent with a financially motivated hacking group. The attacks aim to steal multi-factor authentication (MFA) codes to breach corporate software-as-a-service (SaaS) platforms.
The campaign employs sophisticated voice phishing, known as vishing, combined with fake login pages designed to mimic a victim’s own company. This method allows threat actors to bypass security measures that rely on one-time codes sent via SMS or generated by an authenticator app.
Attack Methodology and Tradecraft
According to Mandiant’s analysis, the threat actors initiate contact with employees via phone calls. The caller impersonates a trusted entity, such as an IT helpdesk technician, and convinces the target to visit a credential-harvesting website. This fraudulent site is tailored to look like the victim organization’s legitimate login portal.
Once the employee enters their username and password, they are prompted to provide the MFA code. The attackers capture these credentials and the code in real-time, granting them immediate access to the corporate account. This access is then used to infiltrate further systems and data.
Link to Known Threat Group
Mandiant stated the tradecraft in these incidents is consistent with operations previously attributed to ShinyHunters. This group is known for financially motivated cyberattacks and large-scale data theft, often followed by extortion demands. The firm’s report indicates the group is now focusing more intensely on compromising business SaaS environments.
The shift towards targeting MFA specifically highlights how cybercriminals are adapting to the increased adoption of this security layer by organizations worldwide. The technique effectively negates a primary defense against account takeover.
Implications for Corporate Security
This development poses a serious challenge to organizations that depend on SaaS applications for critical operations like email, customer relationship management, and cloud storage. A successful breach can lead to data theft, financial fraud, and significant operational disruption.
Security experts emphasize that while MFA remains essential, it is not impervious to social engineering. The human element is often the weakest link in the security chain, and these vishing attacks are designed to exploit it directly.
Mandiant’s disclosure is expected to prompt security teams to review their employee training programs regarding social engineering and vishing attempts. Companies may also consider implementing stronger forms of authentication, such as phishing-resistant FIDO2 security keys, for high-privilege accounts. Further technical advisories from cybersecurity agencies detailing indicators of compromise are anticipated in the coming weeks.
Source: Mandiant