cybersecurity researchers have disclosed a software supply chain attack targeting the Open VSX Registry, a popular marketplace for open-source development tools. The incident, which occurred on January 30, 2026, involved threat actors compromising a legitimate developer’s account to distribute malicious updates to widely used extensions, infecting downstream users with a malware dubbed GlassWorm.
Attack Vector and Malicious Payload
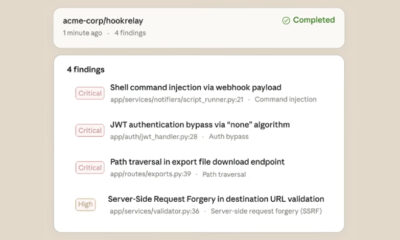
According to the disclosure, unidentified attackers gained control of the account belonging to a developer known as “oorzc.” Using this compromised access, they published malicious versions of four established extensions on the Open VSX platform. These tainted updates contained the GlassWorm malware, which was embedded directly within the extension code.
The attack represents a classic supply chain compromise, where a trusted source in the software ecosystem is subverted to poison the distribution pipeline. By hijacking a real developer’s resources, the threat actors increased the likelihood that their malicious updates would be trusted and installed automatically by users who had enabled automatic updates for their tools.
Scope and Impact on Developers
The Open VSX Registry is a significant platform for the developer community, particularly for those working in open-source environments and with editors like Eclipse Theia. It serves as an alternative marketplace for Visual Studio Code extensions. A successful attack on this registry directly threatens the security and integrity of software development workflows globally.
While the exact number of affected users is not yet confirmed, the use of established extensions suggests the potential for a broad infection. Developers who installed or updated the compromised extensions from the Open VSX Registry on or after January 30 would have inadvertently deployed the GlassWorm malware on their systems.
Response and Mitigation Steps
Following the discovery, the maintainers of the Open VSX Registry were notified and have taken action to remove the malicious versions. Security advisories have been issued to warn the community. Researchers are urging all developers who use extensions from this registry to verify the integrity of their installed tools, particularly those from the affected author.
Standard security recommendations in the wake of such an attack include disabling automatic updates for critical development tools, reviewing extension sources and permissions, and conducting thorough security scans on development machines. Organizations are advised to audit their software bill of materials for any dependencies linked to the compromised extensions.
Broader Implications for Software Supply Chains
This incident underscores the persistent vulnerability of open-source repositories and package registries to supply chain attacks. It highlights how a single compromised account can be leveraged to undermine trust and security for a large user base. The software industry continues to grapple with securing these critical, interconnected ecosystems against increasingly sophisticated threats.
The GlassWorm malware’s specific capabilities and intent are still under analysis by security firms. Previous similar campaigns have aimed at data theft, credential harvesting, or establishing a persistent backdoor for further network intrusion.
Investigations by platform maintainers and cybersecurity firms are ongoing to determine the initial point of compromise and the full extent of the attack. Further technical indicators of compromise and detection rules are expected to be released to help the developer community identify and remediate any infections. The event is likely to prompt renewed discussions on enhancing verification and security protocols for public code registries.
Source: GeekWire