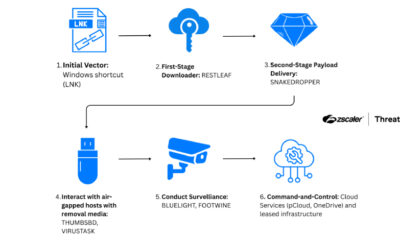
Threat actors are actively exploiting a critical security vulnerability in a widely used npm package for React Native development. The flaw, tracked as CVE-2025-11953 and known as Metro4Shell, was first observed being exploited on December 21, 2025, according to cybersecurity researchers. With a severity score of 9.8 out of 10, this remote code execution vulnerability poses a significant risk to developers and organizations using the affected software.
The vulnerability resides within the Metro Development Server component of the “@react-native-community/cli” package. This package is a core tool for building mobile applications using the React Native framework, which is popular for cross-platform iOS and Android development. The flaw allows remote, unauthenticated attackers to execute arbitrary code on affected systems.
Technical Details and Impact
CVE-2025-11953 is classified as a critical remote code execution (RCE) vulnerability. Successful exploitation grants an attacker the ability to run commands of their choice on a server running the vulnerable version of the Metro development server. This could lead to a complete compromise of the development environment, theft of source code, or deployment of malicious software.
The vulnerability was publicly disclosed by cybersecurity firm VulnCheck, which also first documented its active exploitation. The high CVSS score of 9.8 reflects the ease with which the flaw can be exploited and the high impact of a successful attack, requiring no user interaction or authentication.
Response and Mitigation
Maintainers of the React Native Community CLI have released patches to address the Metro4Shell vulnerability. Developers and organizations are urged to immediately update their “@react-native-community/cli” package to the latest secure version. Security advisories recommend checking all development and build servers for the presence of the vulnerable component.
Standard security practices, such as running development servers behind firewalls and on isolated networks, can reduce the attack surface. However, applying the official patch remains the only definitive solution to prevent exploitation. Security teams are advised to scan their infrastructure for indicators of compromise associated with this campaign.
Broader Security Context
This incident highlights the ongoing security challenges within the software supply chain, particularly concerning open-source development tools. The React Native framework is used by thousands of applications worldwide, making vulnerabilities in its supporting ecosystem a high-value target for malicious actors.
The exploitation of CVE-2025-11953 follows a pattern of attackers rapidly weaponizing newly disclosed flaws in popular development tools and platforms. It underscores the need for developers to maintain vigilant patch management processes, even for tools used in pre-production environments.
Further investigation by security researchers is expected to reveal the full scope of the attacks and the identity of the threat actors involved. The cybersecurity community is monitoring for additional exploit variants and related malicious activity. Organizations should expect continued advisories from software vendors and security agencies as the situation develops.
Source: VulnCheck