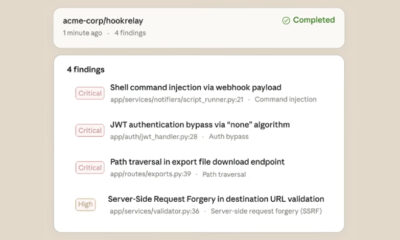
A recent security audit has uncovered hundreds of malicious third-party extensions, known as “skills,” within the ClawHub marketplace, posing a significant data theft risk to users of the OpenClaw AI assistant. The findings, reported by cybersecurity firm Koi Security, identified 341 harmful skills distributed across multiple campaigns, highlighting emerging supply chain vulnerabilities in the open-source ecosystem.
Scope of the Security Breach
Koi Security’s analysis examined a total of 2,857 skills available on ClawHub. The 341 malicious skills discovered were not isolated incidents but part of several coordinated campaigns. These rogue extensions were designed to stealthily harvest sensitive user data from the devices running the compromised OpenClaw assistant.
ClawHub functions as a central repository where OpenClaw users can browse and install skills to add functionality to their self-hosted AI assistant. The platform’s integration with OpenClaw, a popular privacy-focused alternative to commercial AI assistants, made it a high-value target for attackers seeking to exploit trust in the community-driven marketplace.
How the Malicious Skills Operate
The malicious skills leveraged their granted permissions within the OpenClaw environment to access and exfiltrate user information. While the specific data types targeted were not detailed in the initial report, such access typically could include text from interactions, system information, or connected account details. The skills operated by embedding their malicious code within seemingly legitimate skill packages, a classic supply chain attack method.
This incident underscores a critical challenge for open-source platforms: ensuring the security of third-party additions without centralized, proprietary review. Users often assume community-vetted marketplaces are safe, but this audit demonstrates that rigorous, ongoing security scrutiny is necessary.
Community and Developer Response
Following the disclosure, the teams behind OpenClaw and ClawHub are expected to initiate remediation processes. Standard procedure in such cases involves removing the identified malicious skills from the marketplace, notifying affected users, and potentially blacklisting the developer accounts responsible for the campaigns.
Security researchers emphasize that the discovery was made through proactive auditing, not in response to a known breach. This proactive approach helps identify threats before they are widely exploited. However, it also confirms that the threat landscape for extensible, open-source software is evolving rapidly.
Implications for Open-Source Software Security
The situation presents a case study in supply chain risk for decentralized software projects. As projects like OpenClaw grow in popularity, their associated marketplaces become attractive targets for bad actors. The incident highlights the need for enhanced security measures, including more robust code signing, automated security scanning for submitted skills, and clearer user guidelines on risk assessment.
For end-users, the discovery serves as a reminder to exercise caution when installing third-party extensions, even from trusted community sources. Regularly updating software and reviewing installed skills for necessary permissions are recommended basic security practices.
Next Steps and Ongoing Mitigation
Moving forward, the maintainers of ClawHub are likely to review and strengthen their skill submission and vetting procedures. Security analysts anticipate the publication of more detailed indicators of compromise (IOCs) and technical analysis from Koi Security to help users identify if their systems were affected. The broader open-source community may also use this event to discuss standardized security frameworks for similar plugin-based ecosystems to prevent future campaigns of this scale.
Source: Koi Security