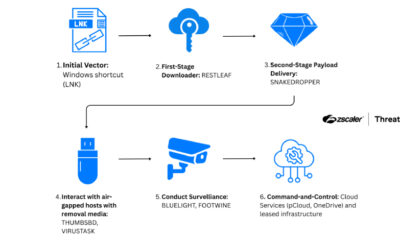
Microsoft has issued a warning that information-stealing malware campaigns are increasingly targeting Apple’s macOS operating system. The tech giant’s security researchers identified a shift in tactics, with attackers leveraging cross-platform programming languages and abusing trusted online platforms to distribute their malicious software.
Expanding Threat Landscape
According to Microsoft’s Defender Security Research Team, these infostealer attacks are “rapidly expanding” beyond their traditional focus on Windows computers. The attackers are now actively developing tools to compromise Mac systems, indicating a broadening of the cyber threat landscape. This expansion poses a significant risk to the large and growing user base of Apple devices in both consumer and enterprise environments.
The malicious campaigns employ social engineering techniques to trick users into installing the malware. One observed method, known as “ClickFix,” presents users with fake error messages. These deceptive prompts convince the user that they need to download a supposed fix, which is actually the infostealer payload. This technique exploits user trust and the desire to quickly resolve perceived technical issues.
Cross-Platform Tactics and Distribution
A key factor enabling this cross-platform shift is the use of programming languages like Python. Python is inherently cross-platform, meaning code written in it can often run on multiple operating systems, including Windows, macOS, and Linux, with minimal modification. This allows threat actors to adapt their Windows-based malware more efficiently for attacks on Macs, reducing development time and broadening their potential victim pool.
Furthermore, Microsoft reports that these groups are abusing trusted platforms for distribution at scale. This involves placing malicious advertisements, often for popular software like productivity tools or games, on legitimate search engines and websites. These fake ads lead users to counterfeit download sites hosting tampered installers. By masquerading as genuine software sources, attackers increase the likelihood that users will download and execute the infected files.
Capabilities of macOS Infostealers
The infostealers targeting macOS are designed to harvest a wide range of sensitive data from infected machines. Once installed, they can collect credentials stored in web browsers, such as usernames and passwords for online banking, social media, and corporate accounts. They also scrape authentication cookies, which could allow attackers to bypass login protections and maintain unauthorized access to online services.
Additional targets include cryptocurrency wallet information and files from the user’s desktop and documents folders. The stolen data is typically exfiltrated to servers controlled by the attackers, who may use it for direct financial fraud, sell it on underground cybercrime forums, or leverage it for further targeted attacks.
Security Recommendations and Response
In response to this growing threat, security experts recommend several defensive measures for macOS users. They advise downloading software only from official vendor websites or the Mac App Store, and to be highly skeptical of ads promoting downloads for commonly sought applications. Users should also be cautious of unsolicited pop-up messages claiming their system has an error that requires an immediate download.
Keeping the macOS operating system and all applications updated with the latest security patches is considered a fundamental practice. Additionally, using reputable security software can help detect and block known infostealer variants. For organizations, enforcing security policies that restrict the installation of unauthorized software and educating employees on these new social engineering tactics are critical steps.
Ongoing Developments and Industry Impact
The cybersecurity industry is monitoring this trend closely, as it represents a notable escalation in threats against the macOS platform, which has historically faced fewer large-scale malware campaigns compared to Windows. The use of adaptable, cross-platform code suggests that threat actors are becoming more sophisticated and efficient in their operations.
Security firms are expected to update their detection algorithms to identify the new Python-based payloads and the distribution networks associated with these fake ads. Collaboration between platform vendors like Apple and Microsoft, along with security researchers, will be crucial in disrupting the infrastructure used in these campaigns and sharing threat intelligence to protect users globally.
Source: Microsoft Security Research