A sophisticated Iranian cyber threat group has resumed its activities with updated infrastructure, following a period of reduced visibility that coincided with a nationwide internet blackout in Iran. The group, tracked as Infy and also known as Prince of Persia, began deploying new command-and-control servers as the government-imposed internet restrictions were lifted in early January 2026.
Security researchers monitoring the group’s activity noted a significant shift. For the first time since its campaigns were first observed, the threat actor ceased maintaining its previous C2 servers on January 8. This pause aligned with the start of the extensive internet shutdown implemented by Iranian authorities. The group’s re-emergence with fresh infrastructure suggests a strategic effort to obscure its operational footprint and evade detection.
Evolution of Tactics and Infrastructure
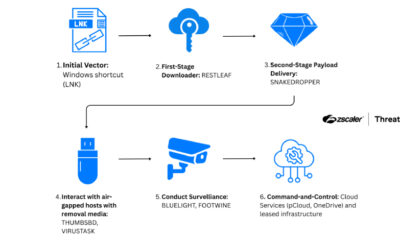
The Infy group is recognized for its persistent and stealthy cyber espionage campaigns, primarily targeting Middle Eastern nations. Its operations often involve sophisticated malware designed to steal sensitive information from government, telecommunications, and technology sector organizations. The latest development indicates an evolution in its methods to maintain operational security.
By abandoning old servers and establishing new ones, the actors make it more difficult for cybersecurity defenders to track their movements and block malicious traffic. This practice, known as infrastructure rotation, is a common tactic among advanced persistent threat groups seeking longevity. The timing of this refresh, immediately following a period of national internet disruption, provides a natural obfuscation event.
Context of the Internet Blackout
The widespread internet blackout in Iran began at the start of January 2026. Such government-imposed shutdowns are not uncommon in the region, often implemented during times of civil unrest or political tension to control the flow of information. The blackout created a global drop in observable internet traffic originating from Iran, affecting both legitimate services and malicious operations.
For cyber threat groups operating within or from Iran, these blackouts force a temporary halt or significant reduction in externally facing activity. The resumption of operations by Infy as connectivity was restored demonstrates the group’s resilience and its capability to quickly adapt its tools and infrastructure to changing circumstances.
Implications for Global Cybersecurity
The return of Infy with new infrastructure has clear implications for international cybersecurity monitoring. Organizations, particularly those in sectors and regions previously targeted by the group, are advised to review their network defenses and threat intelligence feeds. The new C2 servers will need to be identified and blocked by security vendors to prevent successful attacks.
This activity underscores the persistent nature of state-aligned cyber espionage groups. Despite temporary disruptions caused by geopolitical events, these actors demonstrate a consistent ability to regroup and continue their campaigns. Their primary objectives typically remain the theft of intellectual property, government secrets, and intelligence that serves strategic national interests.
Security analysts will now focus on identifying the technical signatures of the new C2 infrastructure and any updated malware payloads. Understanding the communication patterns between infected devices and these new servers is crucial for developing effective countermeasures.
Looking Ahead
Cybersecurity firms and government agencies are expected to intensify their scrutiny of network traffic emanating from Iran in the coming weeks. The discovery and public reporting of Infy’s new servers will likely lead to a race between the hackers attempting to establish persistence and defenders working to dismantle their new footholds. Further analysis may reveal whether the group used the blackout period solely for infrastructure renewal or also for developing new attack techniques. The international cybersecurity community continues to monitor the situation, sharing indicators of compromise to help protect potential targets worldwide.
Source: GeekWire