Docker has released a security update to address a critical Vulnerability in its built-in artificial intelligence assistant, Ask Gordon. The flaw, which could have allowed attackers to execute malicious code and steal sensitive data, affected both Docker Desktop and the Docker Command-Line Interface (CLI). The patch was issued after researchers from Cybersecurity firm Noma Labs privately disclosed the issue, which they codenamed “DockerDash.”
Details of the Security Flaw
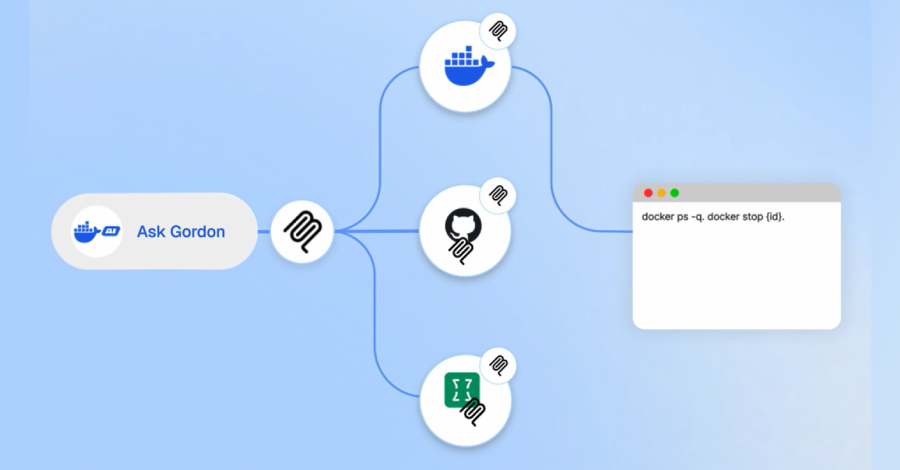
The vulnerability resided within the Ask Gordon AI feature. This tool is designed to help developers by generating Docker commands and offering guidance based on natural language queries. According to the researchers, the flaw was exploitable through manipulated Docker image metadata. An attacker could craft a malicious image with specially designed metadata that, when processed by the Ask Gordon system, could lead to arbitrary code execution on the victim’s host machine.
This type of attack could have severe consequences. Successful exploitation would grant an attacker the same permissions as the user running Docker. This access could be used to exfiltrate sensitive information, such as credentials, source code, or proprietary data stored on the system. It could also serve as a foothold for further attacks within a network.
Response and Remediation
Upon receiving the report from Noma Labs, Docker’s security team moved swiftly to develop and test a fix. The company has since released updated versions of Docker Desktop that contain the necessary patches. Users are urged to update their software immediately to the latest version to mitigate any risk.
Docker has not indicated that the vulnerability was actively exploited in the wild before the patch was made available. The coordinated disclosure process between the researchers and Docker ensured a fix was ready before technical details were made public, limiting the window of opportunity for potential attackers.
Background on Ask Gordon and Docker Security
Ask Gordon was introduced as an experimental AI-powered feature to simplify container management for developers. It analyzes user questions and suggests relevant Docker commands or documentation. While AI integration aims to improve productivity, this incident highlights the new security considerations that such features introduce. The DockerDash flaw specifically targeted the parsing mechanism for image metadata, a core function that interacts with user systems.
Docker containers are widely used to build, share, and run applications. Security within the container ecosystem is paramount, as vulnerabilities can potentially break the isolation between containers and the host operating system. This makes the prompt patching of issues in core components like Docker Desktop critically important for the global developer community.
Next Steps for Users and Developers
All users of Docker Desktop should verify they are running the most recent version. The update process is typically handled automatically through the application’s built-in updater, but users can manually check for updates within the software’s settings. Those using Docker in CI/CD pipelines or other automated environments should also ensure their base images and tooling are updated.
Docker and Noma Labs are expected to publish more detailed technical advisories following standard vulnerability disclosure protocols. The broader security community will likely analyze the patch to understand the exact mechanics of the flaw. This incident serves as a reminder for all software providers to rigorously audit AI-integrated features, as they can introduce novel attack vectors that require specialized security scrutiny.
Source: Noma Labs, Docker Security Advisory