cybersecurity researchers have exposed a sophisticated adversary-in-the-middle framework, known as DKnife, which has been operated by threat actors linked to China since at least 2019. The framework targets routers and edge devices to intercept, manipulate, and redirect internet traffic, enabling the delivery of malware. This activity poses a significant risk to network security globally, as compromised routers can affect all connected users and devices.
Technical Capabilities of the Framework
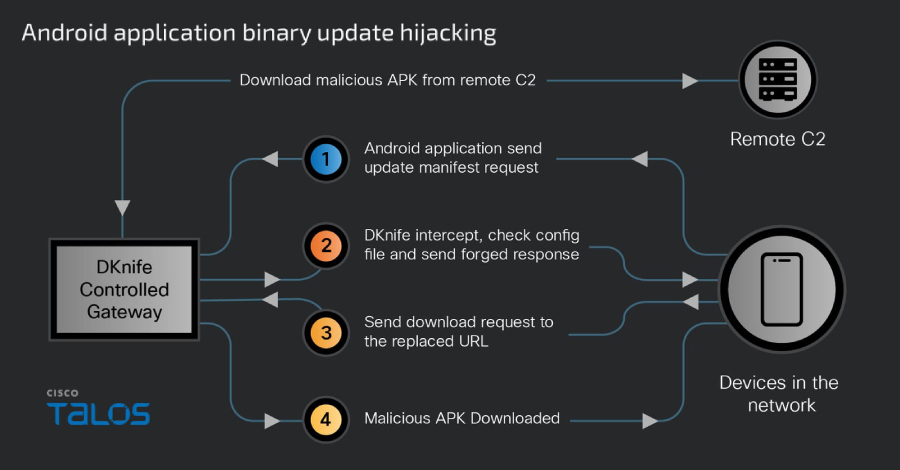
The DKnife framework consists of seven distinct Linux-based implants. These components are engineered to perform deep packet inspection on network traffic passing through an infected device. This allows the operators to monitor communications in detail.
More critically, the framework can actively manipulate this traffic. It can redirect users to malicious websites, inject harmful code into legitimate web pages, and silently deliver additional malware payloads. By targeting the router, a single point of failure, the attackers can compromise every computer, phone, and smart device on a network without needing to infect each one individually.
Attribution and Historical Context
Analysts attribute the development and operation of DKnife to a China-nexus espionage group. Evidence suggests the framework has been in active use for over five years, indicating a mature and sustained cyber operation. Its primary targets appear to be strategic, often focusing on sectors and organizations of geopolitical interest.
The discovery was made public by a team of cybersecurity researchers who have been tracking the group’s infrastructure and tools. Their report provides technical indicators of compromise that network defenders can use to search for infections.
Implications for Network Security
The use of an adversary-in-the-middle framework like DKnife represents an escalation in techniques used for cyber espionage and attack. By compromising network infrastructure, attackers gain a powerful and stealthy vantage point. Traditional endpoint security software on individual computers may not detect activity occurring at the router level.
This threat underscores the importance of securing often-overlooked network hardware, such as routers, firewalls, and gateways. Organizations and even advanced home users are advised to ensure these devices are running the latest firmware, use strong administrative passwords, and have remote management features disabled if not required.
Mitigation and Next Steps
Security firms and researchers are disseminating detection rules and network signatures associated with DKnife. It is expected that major antivirus and network monitoring tools will integrate these indicators into their products in the coming weeks.
Officially, national cybersecurity agencies in several countries are likely to review the technical findings and may issue their own advisories. The continued analysis of DKnife’s code and infrastructure is expected to reveal more about its full capabilities and the extent of its past deployments, potentially leading to further disclosures about affected organizations.
Source: Cybersecurity Research Report