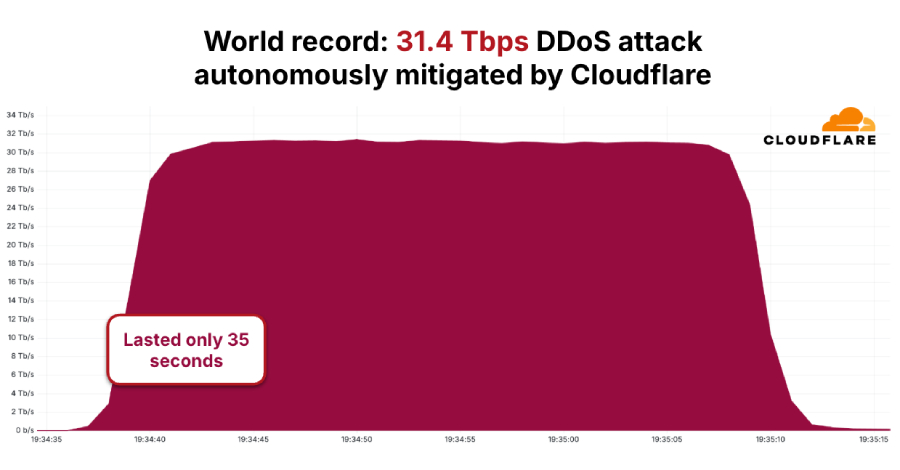
A distributed denial-of-service botnet known as AISURU or Kimwolf has been linked to a record-breaking cyberattack that reached a peak of 31.4 Terabits per second. The attack, which lasted only 35 seconds, was automatically detected and mitigated by the cybersecurity firm Cloudflare.
According to Cloudflare, this incident is part of a rising trend of hyper-volumetric HTTP DDoS attacks launched by the botnet during the fourth quarter of 2025. The company’s systems identified and neutralized the attack traffic before it could impact the targeted online services.
Details of the Record-Setting Attack
The attack’s scale, measured at 31.4 Tbps, represents one of the largest publicly disclosed DDoS events on record. For context, a terabit per second is equivalent to 1,000 gigabits per second, a volume of data capable of overwhelming the infrastructure of most major organizations. The extremely short duration of 35 seconds indicates a highly focused attempt to cause maximum disruption in a minimal timeframe.
Cloudflare reported that the attack traffic was consistent with patterns from the AISURU/Kimwolf botnet, a network of compromised internet-connected devices controlled by malicious actors. These devices, which can include routers, security cameras, and other Internet of Things equipment, are infected with malware that allows them to be remotely commanded to flood a target with junk requests.
The Growing Threat of Hyper-Volumetric DDoS
The term “hyper-volumetric” refers to denial-of-service attacks that generate an exceptionally high volume of traffic, measured in terabits per second. This latest event underscores a significant escalation in the capabilities of malicious botnets. Cloudflare’s data suggests such large-scale HTTP-based attacks from this specific botnet have become more frequent in recent months.
HTTP DDoS attacks work by directing a flood of seemingly legitimate connection requests to a web server or application. The goal is to exhaust the target’s resources, such as bandwidth, memory, or processing power, making the service slow or completely unavailable for genuine users. The use of the HTTP protocol, the foundation of web traffic, can make this attack traffic harder to distinguish from normal user visits.
Mitigation and Industry Response
Cloudflare stated its automated defenses successfully handled the incident without manual intervention. The company’s global network is designed to absorb and disperse massive amounts of malicious traffic, a process known as mitigation. This prevents the attack from reaching the customer’s origin server.
Security researchers often analyze these attacks to understand their origins and methods. The attribution to the AISURU/Kimwolf botnet helps the cybersecurity community track the evolution of specific threat actors. Information about attack vectors and peak sizes is shared within the industry to improve defensive technologies and strategies across different service providers.
Implications for Online Security
The record-setting attack highlights the persistent and evolving threat posed by large-scale DDoS campaigns. While major cloud and security providers have infrastructure to withstand such events, the attack demonstrates the raw power available to cybercriminals. Organizations of all sizes are encouraged to evaluate their DDoS protection strategies, often relying on specialized third-party services to filter malicious traffic before it can cause downtime.
Experts note that the proliferation of insecure IoT devices continues to provide a vast pool of potential bots for these networks. Manufacturers and consumers are urged to follow basic security practices, such as changing default passwords and applying firmware updates, to prevent devices from being conscripted into botnets.
Looking ahead, cybersecurity firms and network operators are expected to continue enhancing their real-time detection and mitigation systems in anticipation of even larger attacks. Official reports and detailed analyses from Cloudflare and other security entities are typically published following such events, providing further technical breakdowns and recommended protective measures for the wider internet community.
Source: GeekWire