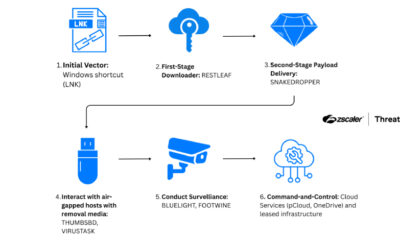
Security researchers have identified a series of emerging cyber threats targeting software development environments, remote administration tools, and cloud infrastructure. These incidents, documented over the past week, represent a shift toward less visible attack methods that exploit trusted systems and routine workflows. The cumulative effect of these smaller signals points to a changing landscape where initial access is increasingly subtle while the potential impact remains significant.
Exploitation of Development and Administration Tools
One prominent vector involves developer workflows. Researchers observed attempts to achieve remote code execution within GitHub Codespaces, a cloud-based development environment. This type of attack could allow malicious actors to compromise a developer’s workspace and potentially move laterally into connected systems or source code repositories.
In a separate but related trend, threat actors continue to abuse legitimate remote administration tools. Instances of AsyncRAT command and control servers being deployed were tracked. This software, while having legitimate uses, is often repurposed by attackers to gain persistent access to infected machines.
A technique known as Bring Your Own Vulnerable Driver (BYOVD) is also seeing abuse. This method involves attackers installing a vulnerable but signed driver on a target system to bypass security protections and gain high-level kernel access. It exemplifies how trusted software components can be weaponized.
Cloud and Identity as Primary Targets
Cloud platforms and identity management paths are under increased scrutiny from attackers. Intrusions targeting cloud access have been documented, where attackers seek to leverage misconfigurations or stolen credentials to gain a foothold in corporate cloud environments. Once inside, they can access sensitive data, deploy resources for cryptomining, or establish a base for further attacks.
Furthermore, attacks are focusing on identity paths, which include single sign-on (SSO) systems, identity providers, and multi-factor authentication (MFA) workflows. Compromising these systems grants attackers broad access across an organization’s applications and data.
The Significance of Routine Actions
Security analysts emphasize that many of these intrusion chains begin with seemingly routine user actions. This could include a developer cloning a repository, an administrator using a remote tool, or an employee authenticating to a cloud service. The surface-level appearance of these actions is not dramatic, which is precisely what makes them effective entry points for persistent threats.
Industry Response and Mitigation
The cybersecurity industry is responding to these trends with updated guidance. Recommendations consistently stress the importance of principle of least privilege access, especially for development and cloud admin accounts. Regular patching of all software, including drivers and development tools, is considered a fundamental defense.
Enhanced monitoring of cloud identity and access management logs is also advised to detect anomalous sign-in attempts or permission changes. For development teams, securing continuous integration/continuous deployment (CI/CD) pipelines and reviewing the security of third-party code dependencies are critical steps.
Looking ahead, security firms anticipate that the blending of attacks across development, cloud, and identity systems will continue. Official advisories on specific vulnerabilities related to these threats are expected as investigations conclude. Organizations worldwide are likely to review their security postures for these often-overlooked attack surfaces, with a focus on detecting low-and-slow intrusion attempts that lack traditional dramatic indicators.
Source: Various cybersecurity research bulletins