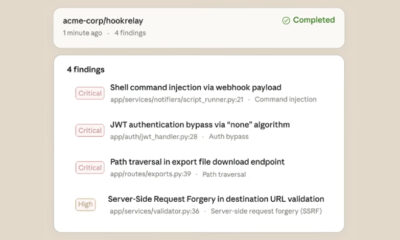
Poland’s national computer emergency response team, CERT Polska, has disclosed a series of coordinated cyber attacks targeting the country’s critical energy infrastructure. The incidents, which occurred on December 29, 2025, impacted over 30 wind and solar farms, a private manufacturing firm, and a major combined heat and power plant.
The affected CHP facility supplies heat to nearly half a million customers, highlighting the potential for significant disruption to essential public services. The disclosure marks a notable escalation in cyber threats against renewable energy assets and industrial control systems within the European Union.
Scope and Attribution of the Attacks
CERT Polska has attributed the coordinated campaign to a known advanced persistent threat actor. While the agency did not publicly name the specific group in its initial announcement, it confirmed the attacks exhibited hallmarks of sophisticated, state sponsored activity. The primary targets were operational technology networks managing the generation and distribution of energy.
The simultaneous targeting of numerous renewable energy sites suggests a strategic intent to disrupt a growing segment of Poland’s power grid. The inclusion of a large manufacturing company indicates the attackers may have been seeking broader industrial intelligence or aiming to cause cascading economic effects.
Immediate Response and Mitigation
Following the detection of the intrusions, CERT Polska worked with the targeted organizations to contain the threats. Standard incident response protocols were activated, including isolating affected systems, conducting forensic analysis, and applying security patches. There have been no public reports of prolonged blackouts or physical damage to the infrastructure as a result of these cyber attacks.
National cybersecurity authorities and energy sector regulators were notified. The agency is coordinating with international partners, including the European Union Agency for Cybersecurity, to share indicators of compromise and tactical information about the attack methods.
Background on Critical Infrastructure Threats
Cyber attacks on energy infrastructure have become a persistent global concern. Similar incidents targeting power grids and industrial facilities have been recorded in Ukraine, the United States, and other nations in recent years. These events often aim to gather intelligence, create operational disruption, or test defensive capabilities.
The renewable energy sector presents unique security challenges. Wind and solar farms are often geographically dispersed and remotely managed, relying on interconnected digital systems for monitoring and control. This can expand the potential attack surface for malicious actors.
Forward Looking Analysis and Next Steps
CERT Polska is expected to release a detailed technical report on the attack vectors used, which likely involved phishing, vulnerability exploitation, or compromised credentials. The findings will inform updated security guidelines for operators of critical national infrastructure, particularly in the energy sector.
Polish authorities are conducting a full investigation to assess the extent of any data exfiltration or system manipulation. The government may review and strengthen cybersecurity mandates for private energy providers. International cybersecurity alliances are likely to monitor this incident closely as a case study in hybrid threats against modern, decentralized energy grids.
Source: CERT Polska