A cybersecurity firm has introduced a new platform designed to provide continuous monitoring of identity usage within enterprise software applications. The announcement was made this week, addressing what industry experts describe as a growing security gap as identity management becomes more decentralized.
The new offering, termed continuous identity observability, aims to discover, analyze, and govern how digital identities are used beyond the scope of traditional identity and access management, or IAM, systems. The core challenge it seeks to solve is the migration of identity logic from centralized directories into individual application code, APIs, and service accounts.
The Evolution of Identity Management
Traditional IAM tools were primarily engineered to govern users within defined corporate directories, such as Active Directory. For years, this model provided a central point of control for employee access to systems and data.
However, the technology landscape for businesses has shifted significantly. Modern enterprises now operate on a vast array of custom and commercial applications, each with its own authentication mechanisms and authorization rules. Over time, the logic controlling who can access what has increasingly been embedded directly into the code of these applications.
The Emerging Security Blind Spot
This shift has created a substantial visibility gap for security teams. While central IAM platforms manage the initial login, they often cannot see how identities are used after authentication, what permissions are invoked within an app, or how service accounts interact with other systems.
Security analysts note that this lack of continuous oversight can lead to privilege creep, where users accumulate unnecessary access rights, and increase the risk of insider threats or compromised accounts going undetected. The decentralized nature of modern application development has effectively placed identity controls outside the traditional identity security stack.
How the New Platform Functions
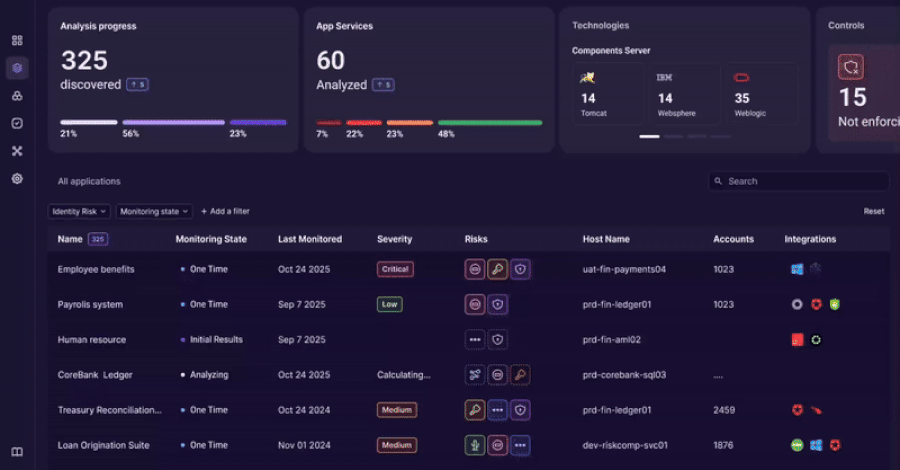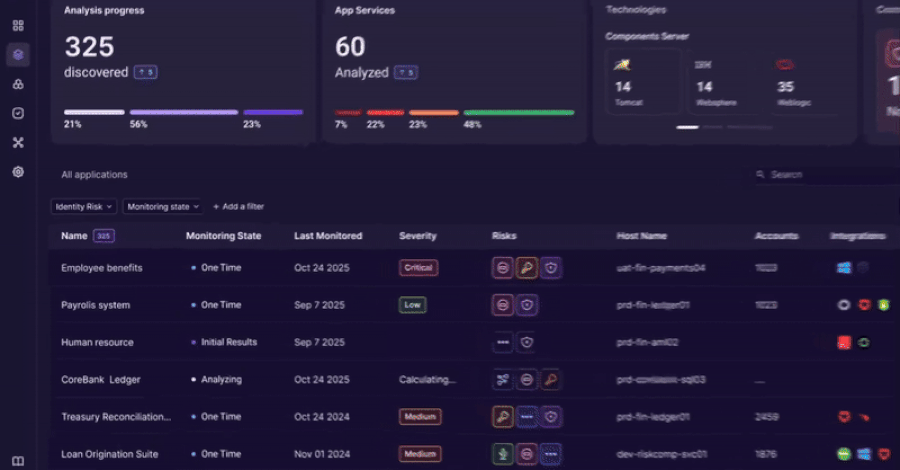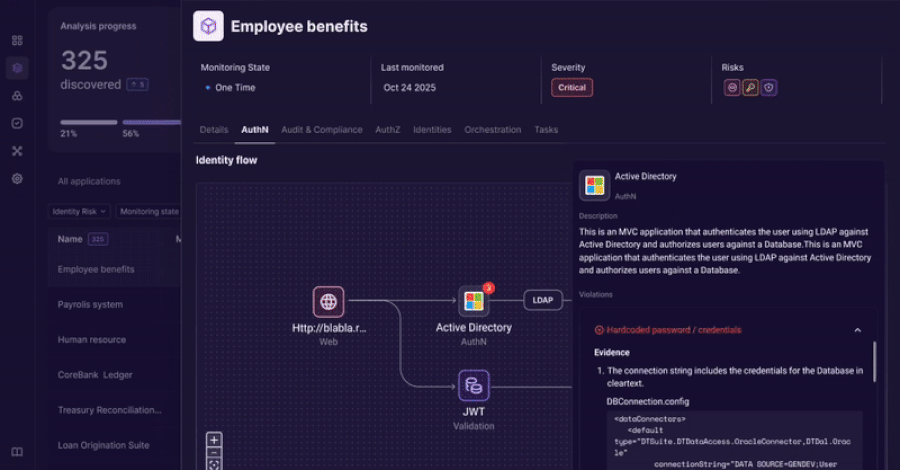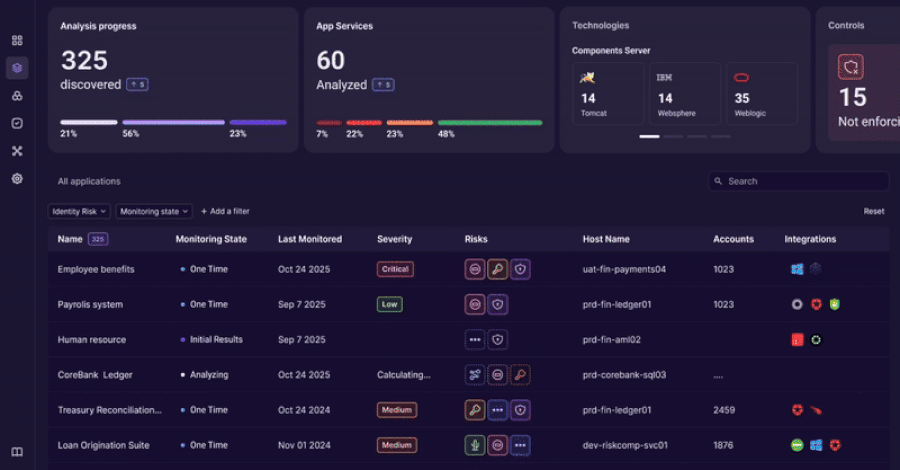
The observability platform works by integrating with an organization’s application environment to provide a real time map of identity interactions. It is reported to automatically discover where and how identities are used across custom code, APIs, and cloud services.
By analyzing this flow of identity data, the tool aims to help organizations enforce governance policies, detect anomalous behavior that could indicate a breach, and maintain compliance with regulatory standards by providing an audit trail of identity activity.
Industry observers suggest the launch reflects a broader trend in cybersecurity toward extending security controls deeper into the development and runtime phases of applications, a concept often referred to as shift left security.
Market Context and Future Developments
The introduction of this platform occurs as businesses globally report increasing difficulties in managing digital identities, which are a prime target for cyber attackers. Several other security vendors are also exploring solutions in the adjacent spaces of cloud infrastructure entitlement management and identity threat detection and response.
According to available information, the company plans to make the platform available to enterprise customers immediately. Further development is expected to focus on expanding integration capabilities with a wider range of development frameworks and cloud service providers throughout the year.
Source: Company Announcement