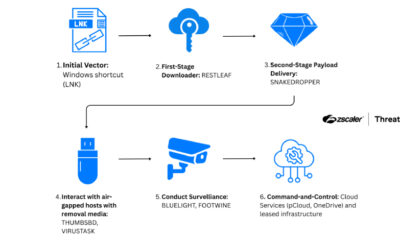
A Russia-linked state-sponsored hacking group has been observed exploiting a newly disclosed vulnerability in Microsoft Office software in targeted attacks across Eastern Europe. The campaign, which security researchers have codenamed Operation Neusploit, marks an early and aggressive use of the security flaw for espionage purposes.
According to a report from cybersecurity firm Zscaler ThreatLabz, the threat actor known as APT28, also tracked as UAC-0001, weaponized the vulnerability on January 29, 2026. The attacks specifically targeted users in Ukraine, Slovakia, and Romania.
Technical Details of the Exploitation
The vulnerability, identified as CVE-2026-21509, is a security flaw within Microsoft Office. While specific technical details of the flaw are limited in the public domain, its exploitation by a sophisticated group like APT28 indicates it is a significant vector for compromising systems. The group leveraged the flaw to deliver malware, a common tactic in cyber espionage campaigns aimed at stealing sensitive information.
APT28, which is widely attributed by Western intelligence agencies to Russia’s military intelligence directorate (GRU), has a long history of conducting cyber operations against government, military, and corporate targets. Their operations often focus on intelligence gathering and are frequently geopolitical in nature, aligning with state interests.
Scope and Impact of the Campaign
The targeting of Ukraine, Slovakia, and Romania suggests a campaign with a clear regional focus. These nations, all situated near Russia’s sphere of influence, have been subjects of cyber activity from Russian-aligned groups in the past. The use of a fresh Microsoft Office vulnerability allows attackers to bypass existing security measures that may not yet have been updated to detect or patch the flaw.
Operation Neusploit exemplifies a common pattern in advanced cyber threats: the rapid adoption of newly disclosed software vulnerabilities by state-sponsored actors. These groups often move quickly to exploit the window between a vulnerability’s public disclosure and the widespread installation of patches by potential targets, a period known as the “patch gap.”
Response and Mitigation
Microsoft has reportedly disclosed the CVE-2026-21509 flaw and issued relevant security updates. Standard cybersecurity guidance applies in such cases: organizations and individuals are urged to apply all available security patches from software vendors immediately. Furthermore, vigilance is required regarding unexpected email attachments or documents, even from seemingly known sources, as these are common delivery methods for Office-based exploits.
Security researchers continue to analyze the malware payloads and infrastructure associated with Operation Neusploit to better understand the full scope of the campaign and its objectives. Attribution to APT28 is based on tactical similarities, infrastructure overlaps, and malware code signatures that align with the group’s known historical activities.
Looking ahead, security analysts expect APT28 and similar threat actors to continue refining their techniques and seeking out new vulnerabilities in widely used software like Microsoft Office. The incident underscores the ongoing need for proactive threat intelligence, rapid patch deployment cycles, and defense-in-depth security strategies for entities operating in regions or sectors of likely geopolitical interest.
Source: Zscaler ThreatLabz